We help solve the manufacturing challenges that matter most
Explore our solutions for your top operational priorities
-
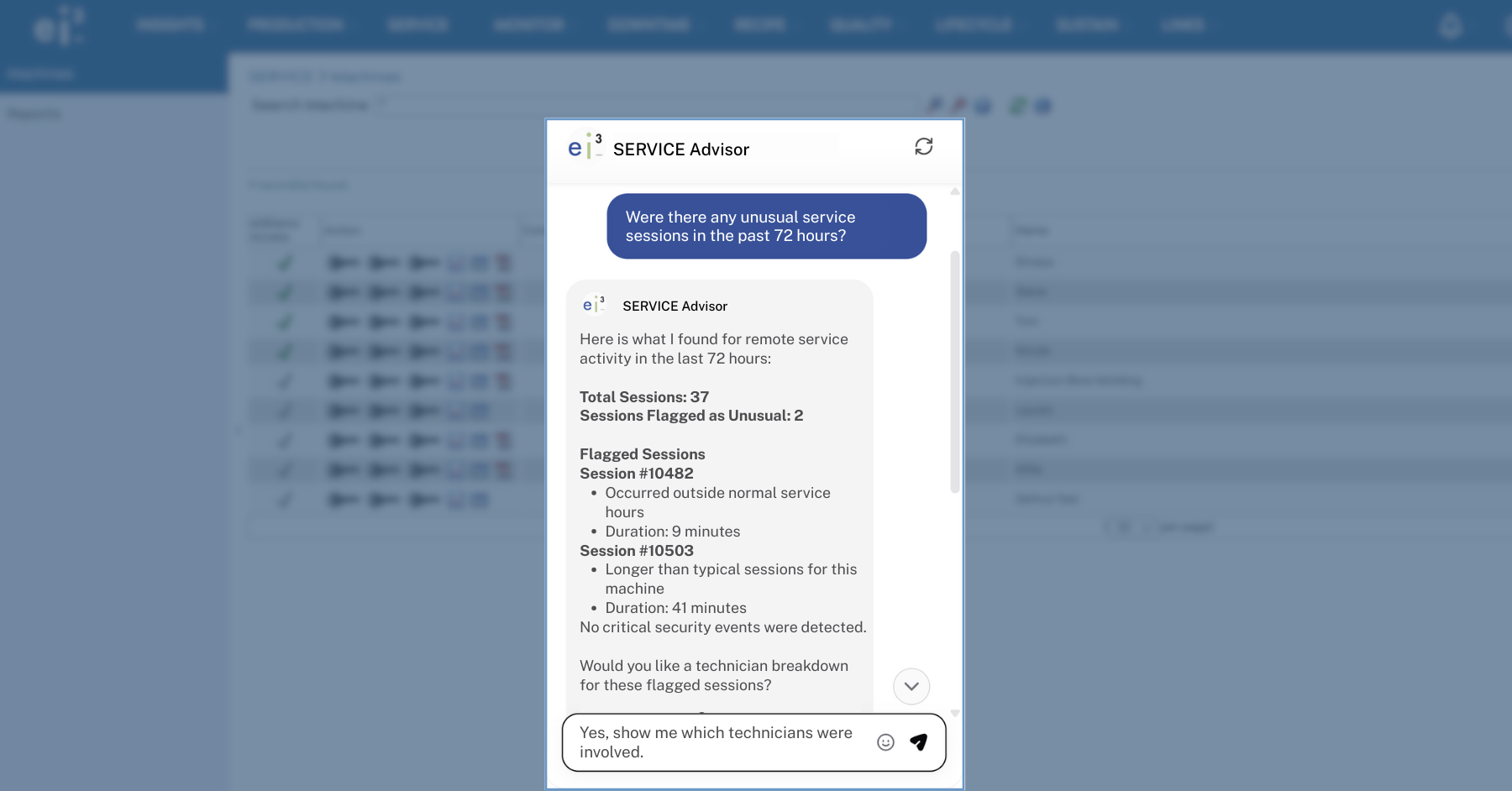
Enable Secure Remote Service
Provide immediate expert support while reducing service costs through secure remote connectivity.
-
Leverage Machine Data
Transform raw machine data into actionable insights that drive operational improvements.
-
Predict Parts and Maintenance
Reduce unplanned downtime through AI-powered predictive maintenance and parts management.
-
Increase Uptime and OEE
Maximize equipment effectiveness through real-time monitoring and advanced analytics.
-
Improve Product Quality
Ensure consistent quality while reducing scrap through automated monitoring and control.
-
Optimize Energy Consumption
Reduce energy costs and meet sustainability goals through intelligent resource management.






.webp)
.webp)