The New Remote Access
Implement secure remote access solutions ready for today's manufacturing challenges.
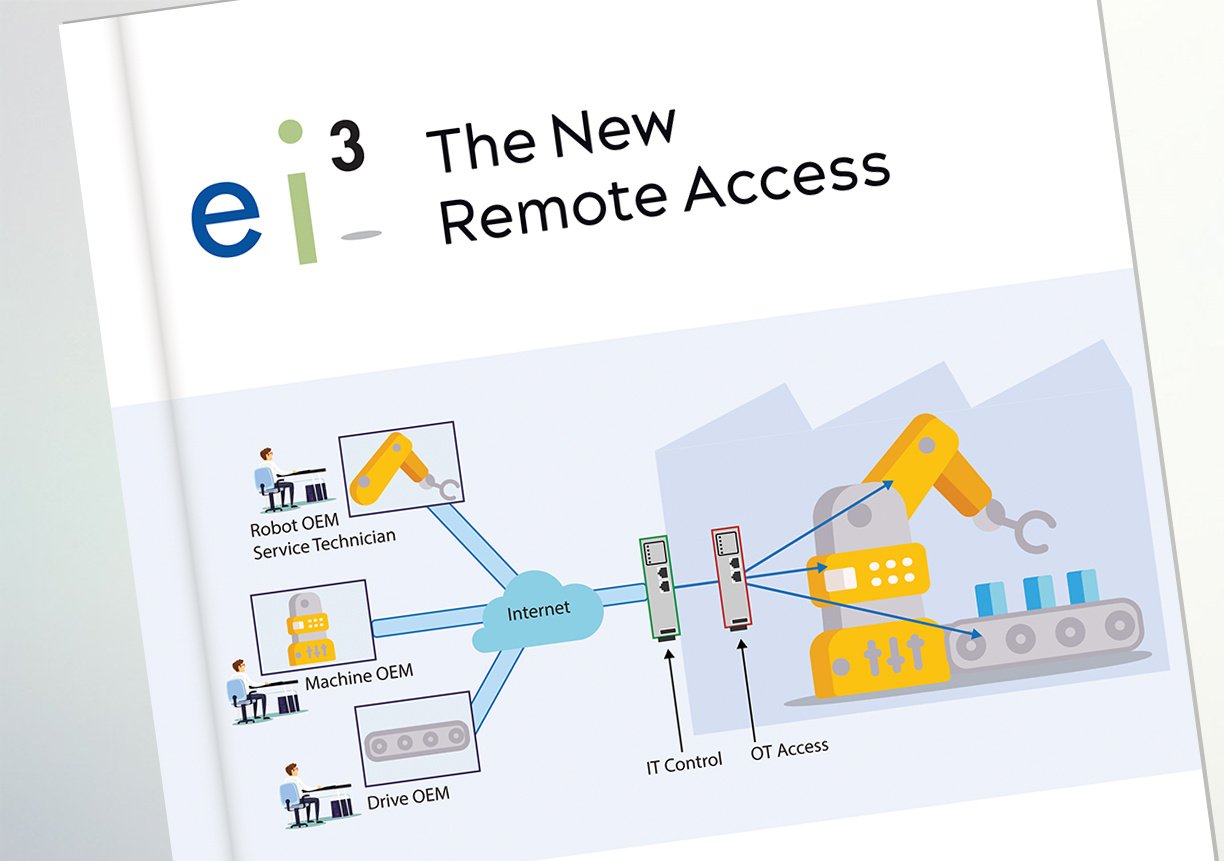
Our comprehensive guide examines the evolution of remote access technologies and provides a structured approach to implementing secure solutions that satisfy both IT and OT requirements.
Our remote access framework ensures:
- Enhanced IT department acceptance
- Complete OT department control
- Future-proof implementation
- Comprehensive security architecture
In this guide, you will discover:
IT and OT compatible architecture
A detailed breakdown of how to design remote access solutions that meet the distinct needs of both IT security teams and operations technology professionals.
Security implementation strategies
Essential deployment recommendations to ensure your remote access capabilities maintain the highest levels of security while delivering operational flexibility.
Checklist for evaluation
Seven critical questions to assess your current remote access solution and identify opportunities for improvement in security, manageability, and flexibility.
Essential IIoT Components
Explore the key components that make digital transformation possible, from secure connectivity to advanced analytics
Kickstart your IIoT journey
Our team is ready to show you how smart technology can help. Whether you're exploring solutions or need support, we're here.
